Introduction
In the first part of our series on information security, we posed the question:
In this second part, we set out the next step for you to consider:
- Where is this information?
Information security is a defensive discipline; however, it is also inherently adversarial. As such, it is vital to keep in mind the point of view of an attacker. An adversary’s success can only occur at specific locations. For example, if valuable and sensitive information is located on a cloud service and associated user devices but the adversary has only compromised a specific device that does not (and cannot) access the information, then they will not succeed.
You therefore have to secure the information everywhere it is located across a wide variety of forms, including paper, digital, and mental.
Forms
You should consider the forms your information takes before looking at the locations of each. In the modern world, information in digital form is the norm; however, the propensity for digital representations of information should not mean that you overlook the security of other forms.
Remember, your adversaries will seek to compromise your information in a variety of ways; they will often try the simplest, cheapest, and most reliable ways first. For example, if you discard a printed copy of a document, then searching your refuse will allow them to achieve their goals without having to expend the effort of compromising any systems. Interrogating people with knowledge of the information will be equally effective. Again, this is about considering the adversary’s point of view rather than relying solely on a defensive stance.
It is generally quite obvious where information is located in physical form. In contrast, the digital realm is complex and opaque. Many experienced technology experts are unaware of the underlying complexity of many systems and the additional copies created when using those systems. This duplication is generally seen as a positive thing when it comes to functionality, but is extremely challenging when it comes to security. These multiple copies need to be considered alongside more-obvious digital representations of your information.
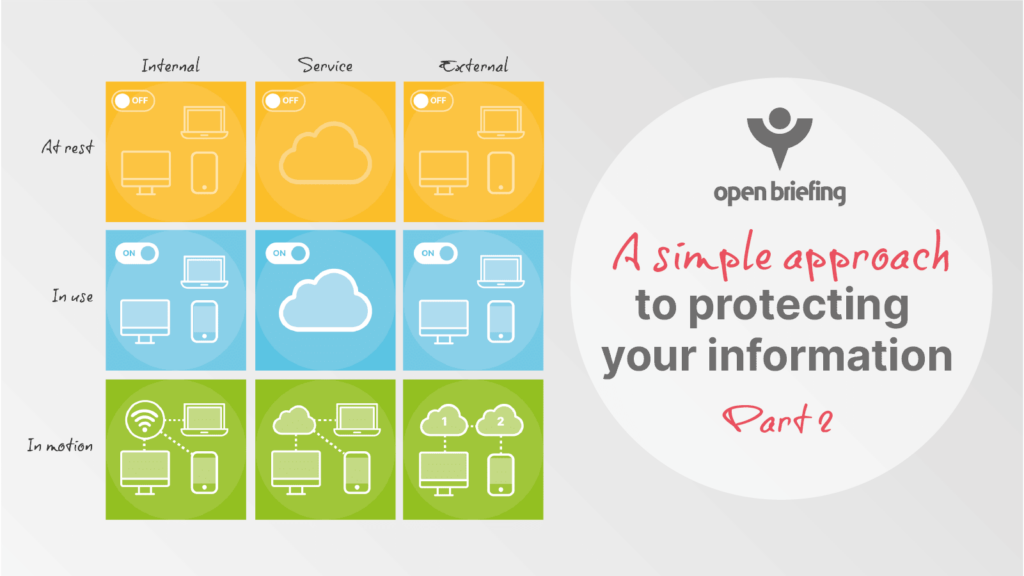
States
The complexity of digital information is compounded by the fact that data can also be in one of three states:
- At rest: On a powered-off device.
- In use: On a powered-on device.
- In motion: Being transferred between two devices.
This is not academic; it is absolutely vital that you understand the distinction between the first and second items. For example. many cloud services will advertise encryption at rest. This implies that the information is encrypted on the service provider’s side (and is often mistaken by users as end-to-end encryption). However, this is only the case if their systems are powered off and the data is at rest. Additional claims of near 100% service availability (or uptime) means that your data will not be at rest but rather in use – and thus not encrypted – nearly all the time.
Location
Alongside states, an additional distinction regarding digital information is the location:
- Internal: On devices you or the organisation own and control.
- Services: Devices owned by a third party but partially within your control.
- External: On devices you or the organisation have no control over.
While you may have some control over the internal devices and services that you use, your information may exist on numerous external devices that you have no control over. External devices include personal devices, devices belonging to those you share data and communicate with, and the services used by these devices. It is crucial that you determine if your valuable or sensitive data is located on any external devices, as you may not be able to do anything about it now. The best option here is prevention.
Conclusion
You should now be in a position to answer the following questions:
- What is your most valuable and sensitive information?
- Where is it located in all forms and states?
If you are unable to locate your most valuable and sensitive information, then you cannot expect to secure it. This is because adversaries will look in many places until they find it. They may collect information from others, service providers, or even search engines to see if they already have or can easily find what they want.
In the next article, we will examine some simple but very-effective security measures. The first is to reduce the number of copies of information and the time when it might be vulnerable. This has two crucial benefits:
- It provides fewer opportunities for the adversary to be successful.
- It may reduce the breadth and depth of the other security measures required.
The second benefit is key, as it can turn an impossible task into one that is feasible, even with limited resources. It also provides simplicity, which is the best friend of security.
We are hiring information security consultants! Learn more.