 Introduction
Introduction
In the first part of our new series on information security, we set out a simple approach to help you archive, back up or destroy a lot of the information that may be causing you concerns. You can then focus your energy (and limited resources) on rolling out appropriate security measures for the information that you work with. First, in this article, we must help you answer:
- What is your most valuable and sensitive information?
Information security is fast becoming one of the biggest issues modern charities face. Unfortunately, the concern is not being translated into actions. This situation results from a number of factors:
- The vast amount of information already accumulated.
- The uncontrolled creation and acquisition of information going forward.
- Lack of resources (or lack of budget allocation to information security).
- Unwillingness or inability to change.
- Hope that a few tools will protect everything from every possible attack.
- Confusion about what to do.
It is essential that a start is made as soon as possible because the challenge will only become greater with each passing day. The reality is that it will not be possible to protect all your information from every possible way it could be compromised, and so you must prioritise. The first step is to identify what you are trying to protect and why.
When tackling this problem, it is often helpful to distinguish between two types of information assets based upon the role they play within your organisation:
- Operational: Ensuring your organisation functions administratively.
- Strategic: Achieving your organisation’s desired change in the world.
This distinction may have some grey areas, but in general this is a good way to partition your organisation’s information assets so that they can be tackled separately.
[click_to_tweet tweet=”The first step is to identify what you are trying to protect and why.” quote=”The first step is to identify what you are trying to protect and why.”]
Value
Information security is often framed in a negative light. For example, it is often seen as prohibitory by forbidding certain ways of working or using certain tools that people like. It is also often seen as a dictator, imposing constraints and making people’s jobs harder than they need to be. If this is your perception, then it is likely the advice you have received to date has not taken into account an essential element: the value information plays in your work.
Some of your information will have value in the efficient operations of your organisation, such as payroll or human resources. It is likely that legal and financial obligations will play a large role in the solution to protect this operational information. Other information will underpin your advocacy work. Simply highlighting a problem will not gain traction with the public or those in power you seek to influence; evidence for your position is essential to successful advocacy. As such, this information is required to achieve your strategic objectives.
Strategic information is not static. It needs to be shared with the right people and used to create new information, such as reports, infographics, and campaigns that will resonate with a target audience. Activities involving high-value information assets may be carried out in a less-secure manner when justified by the desire to realise an asset’s full strategic value. However, while you will receive the credit when things go right, you must also accept responsibility if things do not go to plan. Accordingly, alongside value, you should consider the harm that could result if things go wrong.
Harm
Charities striving to achieve positive change in the world are not seen by all in a positive light. Changing the status quo inevitably means some, who are happy with the current state of affairs, will be threatened by your actions. While the potential harms may sometimes be limited to negative feelings or apathy, some consequences can be much more severe. While some of your activities may be based on publicly-available information, others may require input from confidential sources. Whistleblowers who provide evidence of wrongdoing often face the greatest risk.
There must be some consideration of the risk taken by people who work with you. Those who trust you with information deserve some measure of protection from you. You should consider the potential harms that could arise from a compromise of the security of this information. These consequences could range from inconvenience to potential regulatory fines for your organisation; they may also include the source losing their job or even facing criminal proceedings. In the most severe cases, the source or a member of your staff may face reprisals for their actions in the form of injury, kidnap, torture or death.
While it is essential for you to consider what the worst–case scenario is, not all your information will lead to these serious harms if compromised. So, you should also consider likelihood when prioritising your information assets.
Likelihood
It is often said that security is too expensive and time consuming when it is not necessary but very cheap and worthwhile when it is required. Unfortunately, we can never know for sure when it will be required, and so we must proceed systematically on the basis of risk rather than certainty. Determining the likelihood of something happening is not a science but neither is it arbitrary.
When it comes to the value of information, you should determine both the potential value it could have and when you expect to realise this potential value. For example, information that has been retained for years and not used is unlikely to be of high value to your organisation in the future. This is not to say that the information is not inherently valuable, but rather its value may be lower with respect to your organisation’s other planned activities and priorities.
When it comes to harm, there can be many factors that will determine whether something is likely to happen or not. You should consider who the adversary is, what harm they intend to inflict, and whether they have the capabilities to inflict that harm. You will also need to judge whether they would actually inflict the harm even if it is within their capabilities to do so. For example, negative publicity may deter certain actors – for example, corporations – from acting in a particular way, while other actors – such as governments, organised crime gangs, and vocal pressure groups – may have no such inhibitions.
Next steps
You should consider the different types of information that you hold and seek to better understand both their value to your work and the harms to you and others that could result from an attacker compromising them.
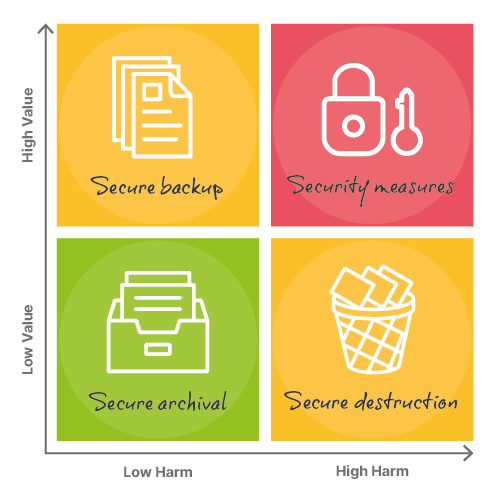
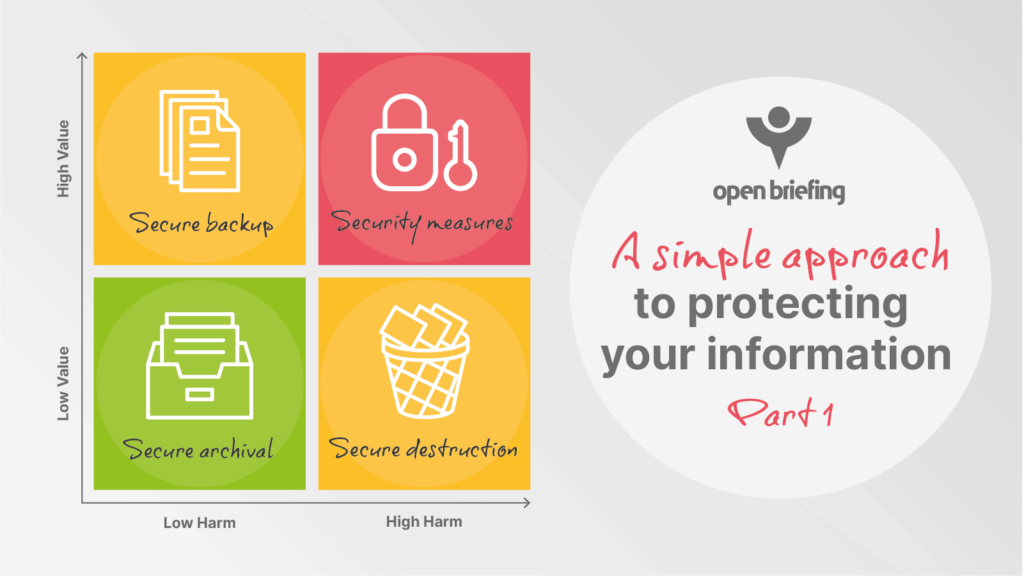
While there are a number of possible risk-scoring systems that could be used to decide where to start, a simplified approach is usually best at this stage. The approach can become more sophisticated and detailed as necessary over time. The diagram here sets out four broad categories of action based on the potential value and harms of your different information assets.
Information with a low value and a low potential for harm should be considered for secure archival, while information with a low value but high potential for harm should be considered for secure destruction. High-value information with a low potential for harm might benefit from limited secure backups to protect against accidental or malicious destruction or modification.
High-value information that could lead to serious harm is a little more complex, and is a good place to begin to roll out appropriate security measures. If you are unwilling or unable to make a single improvement to the security of your most sensitive and valuable information, then you must ask why? (Is it because you cannot identify this information?)
[click_to_tweet tweet=”If you are unwilling or unable to make a single improvement to the security of your most sensitive and valuable information, then you must ask why?” quote=”If you are unwilling or unable to make a single improvement to the security of your most sensitive and valuable information, then you must ask why?”]
Conclusion
By considering the value and potential harms of your operational and strategic information and the likelihood of that value or harms being realised, you should also be in a position to take some actions based upon this initial assessment, including:
- Secure archival.
- Secure backup.
- Secure destruction.
You will have then archived, backed up or destroyed a lot of the information that may have been causing you concerns. This is a fantastic starting point! You can now focus your energy (and limited resources) on rolling out appropriate security measures for the most valuable and sensitive information that you work with. In the next article, we help you first answer the question: where is this information?